Who can assume an IAM Role?
AWS IAM roles can be assumed by principals. AWS has a complex syntax to specify which principal is able to assume a role within the account and cross-account.
Example
CodeShield's policy evaluation engine evaluates which concrete resource or identity is capable of assuming a particular role. To understand who can assume a role, inspect the properties of an AWS:IAM:Role in the Inventory. Each role has a property assumeRolePolicyDocument. This data is from the AWS console/API enriched by the information that CodeShield policy evaluation engine computed.
In the example below, there is a demo-role. The role can be assumed by the principal referenced by arn:aws:iam::317098767149:root. This is the information given by the AWS API. On top of that, CodeShield evaluates the set of IAM users that this string actually refers to. In the example below, there are four users who can assume the role.
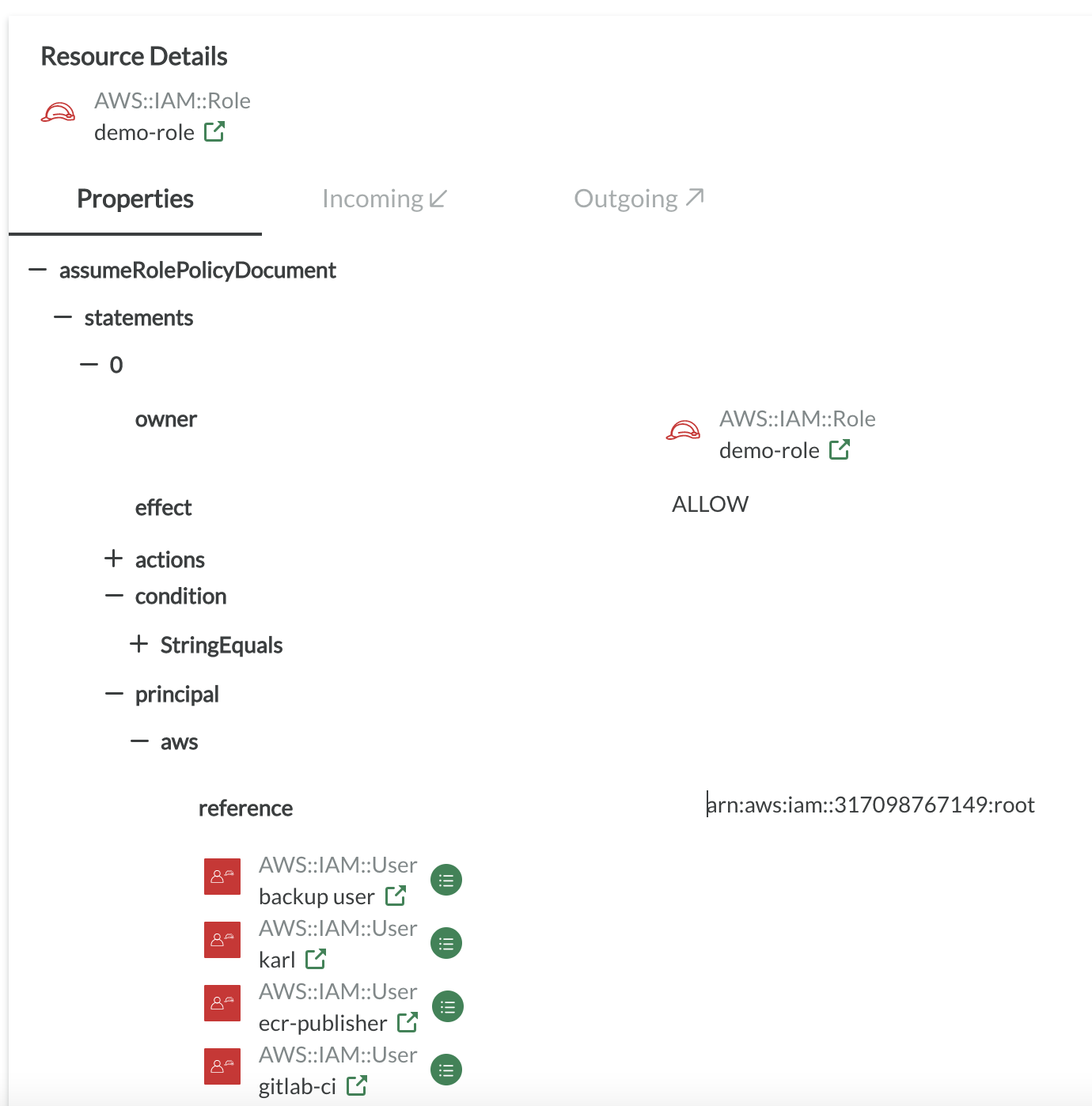
Note that the principal section of a trust policy only define which principals can assume the role from the view of the role. It is not yet policy evaluated, i.e., if the principal has an identity-based policy that explicitly denies assuming roles, the principal cannot actually assume the role, event though the trust policy allows it. To check which principals can indeed assume a role, lookout for a AccessRef that allows 'sts:AssumeRole' in its 'relevantActions' section. If the 'sts:AssumeRole' action is not present or there is no AccessRef between Principal and Role, the role cannot be assumed by the Principal!